Liferay Portal Json Web Service Deserialization Vulnerability (CVE-2020–7961) Analysis | by Knownsec 404 team | Medium

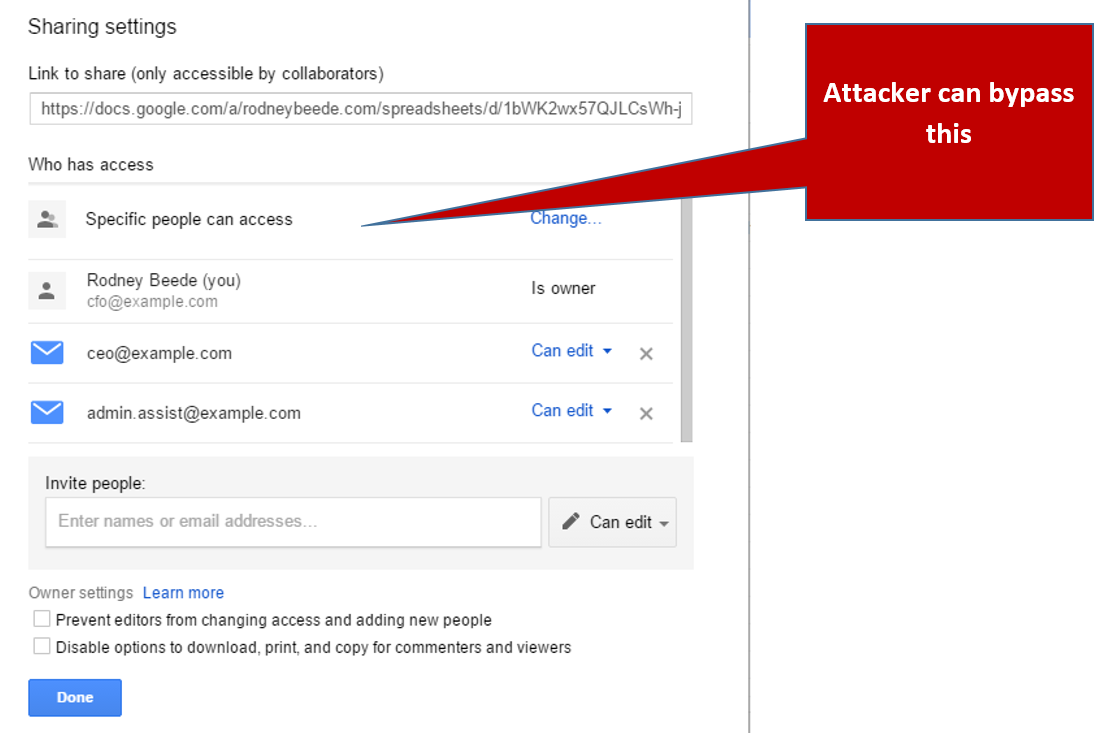
Kevin Beaumont on Twitter: "Also for balance - the mitigation shown in the block of blocking Powershell in autodiscover.json should be fixed in ProxyShell patches. Screenshot from blog and my tweet from
Update update-notifier to resolve got vulnerability CVE-2022-33987 · Issue #1343 · typicode/json-server · GitHub
vulnerability-rating-taxonomy/remediation_advice.json at master · bugcrowd/ vulnerability-rating-taxonomy · GitHub
10 API Security Vulnerabilities You Need To Be Aware Of (Along with REST API Overview) | by Santosh Shinde | JavaScript in Plain English
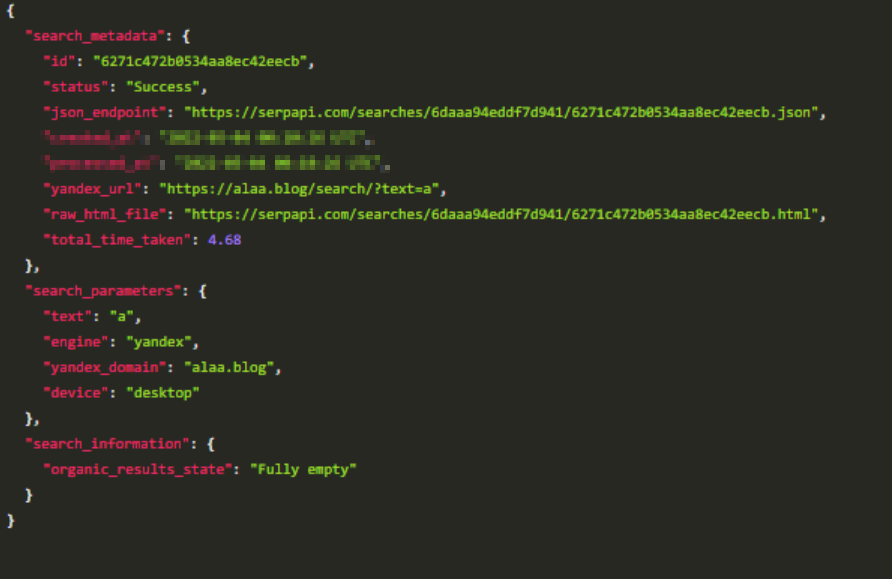
failed to get the vulnerability: failed to marshal JSON: unexpected end of JSON input' warning with some images · Issue #1691 · aquasecurity/trivy · GitHub

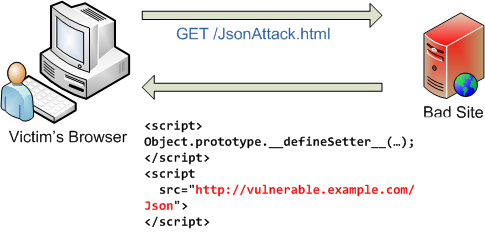
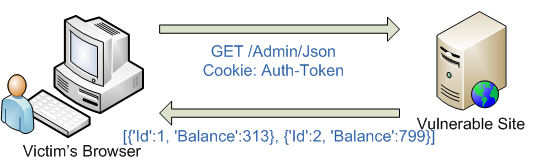
Remote code execution vulnerability exposed in popular JavaScript serialization package | The Daily Swig